
Using TOR to Bypass Port Scan Blocking Protection Firewalls.
This guide will help you bypass port scan blocking firewalls using the dark web, TOR.
The Linux distro we are using is Kali Linux.
If you prefer video format, please check out the video links at the top or our YouTube channel.
Step 1: Download the GitHub Repo
Open your linux terminal, install git with sudo apt install git. Then, download the code by using git clone https://github.com/NorthInfosecTesting/tor_port_scan.git.
Step 2: Install the Requirements
Once the GitHub Repo is downloaded, you need to ensure any prerequisites are installed.
- Change directory to the downloaded tor_port_scan directory by entering
cd tor_port_scan - Install TOR by entering
sudo apt install tor - You may need to uncommect
ControlPort 9051from the file/etc/tor/torrcby removing the#from#ControlPort 9051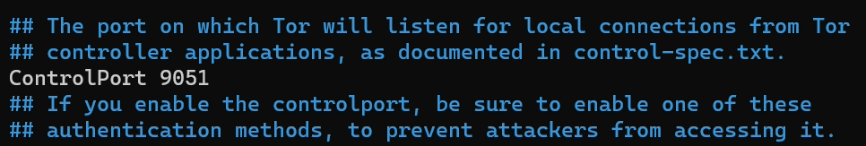
- Enter
sudo systemctl restart tor, thensudo systemctl start tor - Ensure pip and python3 is installed, and enter
python3 install -r requirements.txt
Step 3: Script Parameters
Now the requirements are installed, the TOR port scan python script is ready to run. However, first lets check what parameters can be passed to the script.
python3 scan.py -hwill bring up the usage menu.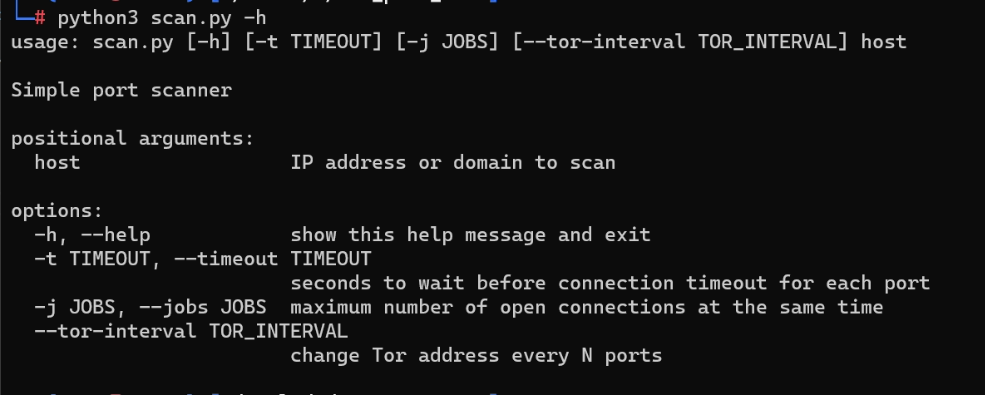
python3 scan.py [target]will execute a port scan changing the TOR address every 5 ports.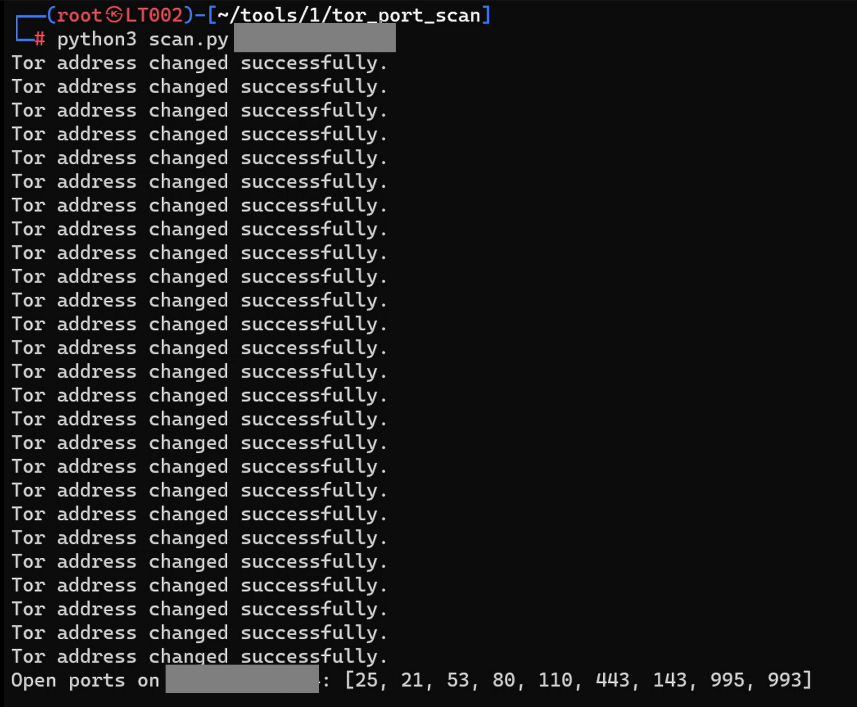
- You can use the
--tor-interval [n]flag to change the number of ports scanned before the TOR IP address is changed. For example,python3 python3 scan.py --tor-interval 10 [target] - The timeout
-tflag can be used to enter the TIMEOUT seconds to wait before connection timeout for each port. - The jobs
-jflag can be used to set the maximum number of open connections at the same time.
Now that you know port scan blocking can be bypassed, lets see what we can find with an external pen test.